Penetration Testing Services
Internal & External Network Penetration Testing, Web App Penetration, and Social Engineering
Every 39 seconds there is another cyber attack. Cybercriminals are utilizing robust tools and sophisticated techniques to attack businesses and steal data. Knowing your own weaknesses is critical to preventing disaster before it is too late.
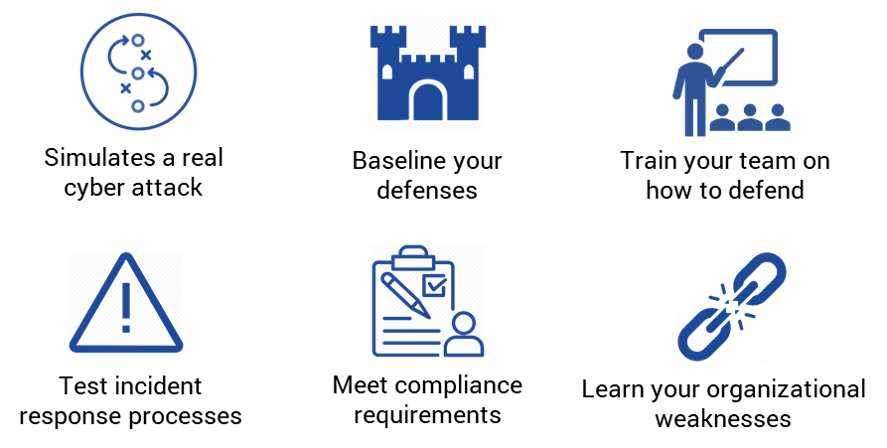
Penetration testing simulates real-world attacks which identify points of exploitation and test your defensive mechanisms. The primary goal of a penetration test is to evaluate your overall security posture.
At Appalachia Technologies our ethical hackers are some of the best and brightest in the business. Our team consists of highly certified cybersecurity experts who can reveal hidden vulnerabilities before hackers do. They use the same methods and tactics that cybercriminals would use, such as exploiting software vulnerabilities, bugs, misconfigured devices, and other operational weaknesses. Our Certifications include: Comptia Security +, eLearn Security Junior Penetration Tester, Certified Ethical Hacking (CEH), Certified Ethical Hacking Forensic Investigation (CEH-FI), Certified Information Systems Security Professional (CISSP), Cisco Certified Network Professional Security (CCNP - Security), and more.
Offense Over Defense: More Than Just Telling You What is Out of Date
Penetration testing and vulnerability scanning are often confused for the same service. A vulnerability scan is an automated, high-level test that looks for and reports potential vulnerabilities, categorized by criticality. A penetration test is an exhaustive, live exercise designed to exploit weaknesses in your system.
Why Penetration Testing?
Find Weaknesses that Social Engineering Can Exploit
Cybercriminals use social engineering tactics to trick users into granting them access. These tactics include phishing/spear phishing, baiting, and tailgating. In other words, the attacker will strike at your users and try to hit their emotions to gain sensitive information. Our team can mimic these types of attacks and help you strengthen your defenses through training and policy.
Our Approach
The Penetration Testing Execution Standard (PTES) is the premiere framework for penetration testing companies. This standard provides guidance on penetration testing processes and techniques and is the most complete standard on the subject today. Our ethical hackers adhere to the PTES guidelines to ensure you receive consistent and actionable results from our penetration tests that will help make your company more resilient to cyber-attacks. Our team specializes in ensuring our standards always align with industry best practices and are using the latest tools and techniques that unethical hackers may be using to try and breach your defenses.
Our Web Application Penetration Testing follows the industry best practice set forth by the Open Web Application Security Project (OWASP) and the Web Application Hackers Handbook. This standard was created by industry leading professionals as a standard for how web application penetration testing should be conducted and organized. We test for everything from common flaws to advanced web application issues
