Penetration Testing Overview
Every 39 seconds there is another cyber attack. Knowing your own weaknesses is critical to preventing disaster before it is too late. Cybercriminals are utilizing robust tools and sophisticated techniques to attack businesses and steal data. Knowing your own weaknesses is critical to preventing disaster before it is too late. At Appalachia Technologies, our ethical hackers are some of the best and brightest in the business.
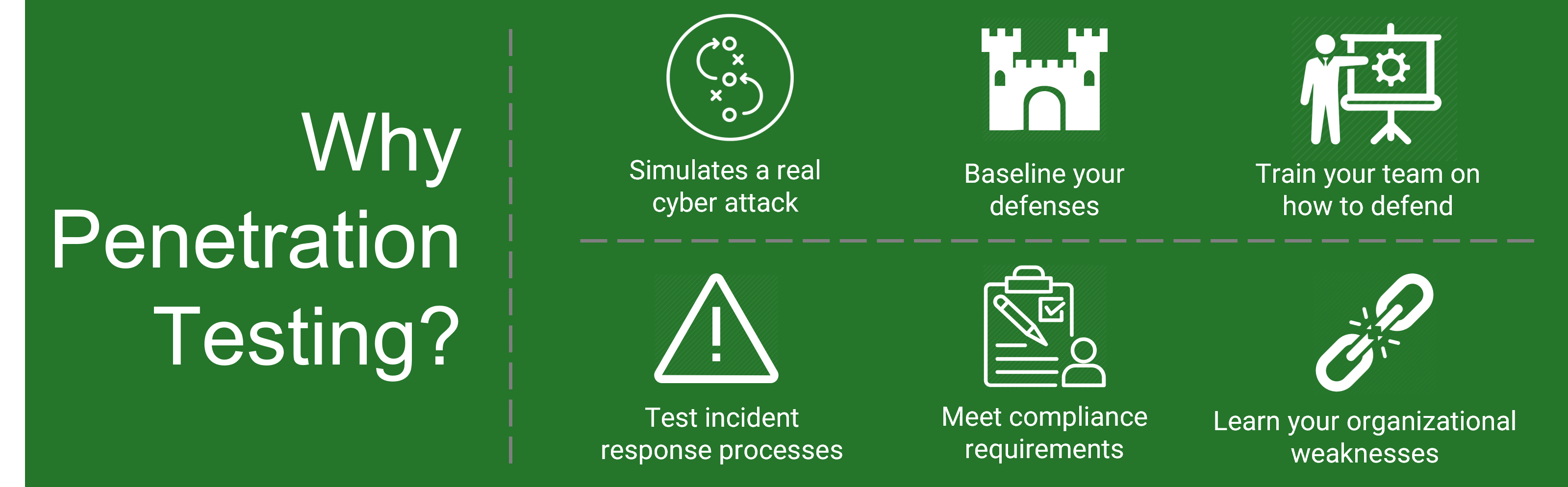
WHY PENETRATION TESTING?
Penetration testing and vulnerability scanning are often confused for the same service. A vulnerability scan is an automated, high-level test that looks for and reports potential vulnerabilities, categorized by criticality. A penetration test is an exhaustive, live exercise designed to exploit weaknesses in your system.
Both vulnerability scanning and penetration testing can feed into a cyber risk analysis process and help determine controls best suited for the business, department or practice. They must work together to reduce risk, but to get the most out of them, it is very important to know the difference, as each is important and has a different purpose and outcome. 1
1 https://www.tripwire.com/state-of-security/difference-vulnerability-scanning-penetration-testing
NETWORK PENETRATION TESTING
The Penetration Testing Execution Standard (PTES) is the premier framework for penetration testing companies. This standard provides guidance on penetration testing processes and techniques and is the most complete standard on the subject today. Our ethical hackers adhere to the PTES guidelines to ensure you receive consistent and actionable results from our penetration tests that will help make your company more resilient to cyber-attacks. Our team specializes in ensuring our standards always align with industry best practices and are using the latest tools and techniques that unethical hackers may be using to try and breach your defenses.
Our Red Team consists of highly certified cybersecurity experts and CEH (Certified Ethical Hackers) who can reveal hidden vulnerabilities before hackers do. They use the same methods and tactics that cybercriminals would use, like exploiting software vulnerabilities, bugs, misconfigured devices, and other operational weaknesses. Ranging from:
|
· Common attack vectors · Known exploits · Common misconfigurations · Brute force attacks |
· Man-in-the-middle attacks · Active phishing attacks · Browser exploitation · USB drops |
Deliverables include an extensive technical report with all of our recommendations and findings, along with an Executive-level presentation.
WEB APPLICATION PENETRATION TESTING
Web applications today are at the heart of many organizations. Protecting these web applications from cyber criminals is critical. At Appalachia Technologies, our Web Application Penetration Tests can ensure you know where your weaknesses are before the bad guys can take advantage of them.
Our penetration testing or red team exercises follow the industry best practice set forth by OWASP and the Web Application Hackers Handbook. This standard was created by industry-leading professionals as a standard for how web application penetration testing should be conducted and organized. We test for everything from common flaws to advanced web application issues:
|
· Injection attacks · Broken authentication · Sensitive data exposure · Broken access control · Common security misconfigurations · Client-side controls
|
· Access controls · Logic flaws · Authentication mechanisms. · Session management mechanisms · Web server vulnerabilities · Input-based vulnerabilities · Cross-site scripting, and more! |
If all of this talk on penetration testing has your wheels turning, complete the form to the right for a consultation!
 Mike Miller is a cybersecurity professional with 25 years of experience throughout the IT industry. He has focused on security, specializing in the areas of Virtual Chief Information Security Officer services, Governance, Risk, and Compliance, PCI, SOC, Intrusion Detection, Penetration Testing, and Incident Response. In 2011, Mike founded Cyber Protection Group, which was acquired by Appalachia in 2022. Mike is passionate about mentoring and assisting aspiring cybersecurity professionals and can be found regularly sharing insight on his LinkedIn profile. When he isn’t fighting cyber crime, Mike loves spending time with his wife and kids, often boating in the Ozarks.
Mike Miller is a cybersecurity professional with 25 years of experience throughout the IT industry. He has focused on security, specializing in the areas of Virtual Chief Information Security Officer services, Governance, Risk, and Compliance, PCI, SOC, Intrusion Detection, Penetration Testing, and Incident Response. In 2011, Mike founded Cyber Protection Group, which was acquired by Appalachia in 2022. Mike is passionate about mentoring and assisting aspiring cybersecurity professionals and can be found regularly sharing insight on his LinkedIn profile. When he isn’t fighting cyber crime, Mike loves spending time with his wife and kids, often boating in the Ozarks.
