Appalachia Technologies Blog
NIST CSF 2.0 (Part 1) – What’s Changed and What to Do About It
The NIST (National Institute of Standards and Technology) Cybersecurity Framework, developed in early 2014, is a framework widely respected and used across organizations in the United States. Over the years, revisions have been made – version 1.1 was drafted in 2017 and adopted in 2018, and talk around a more significant update in the form of 2.0 began sometime in 2023. And finally, this February the NIST CSF 2.0 was officially released – so what does this even mean? And why does it matter?
Let’s start by looking at why the CSF was created and its originally intended audience before we look at the latest updates. The NIST CSF was originally created for the finance and manufacturing industries, or critical infrastructure, to establish strong cybersecurity standards. As you read through the first version and its update, you will notice the language used aligns to those industries. Over time, the CSF was recognized as a strong framework that could be adapted to other industries as well that do not already have cybersecurity standards. And while it is adaptable, version 1.1 still presented challenges for small businesses that stem back from its original creation. Ten years later, the cybersecurity landscape has progressed significantly and the NIST CSF has had no other choice but to change as well.
Enter NIST CSF 2.0…
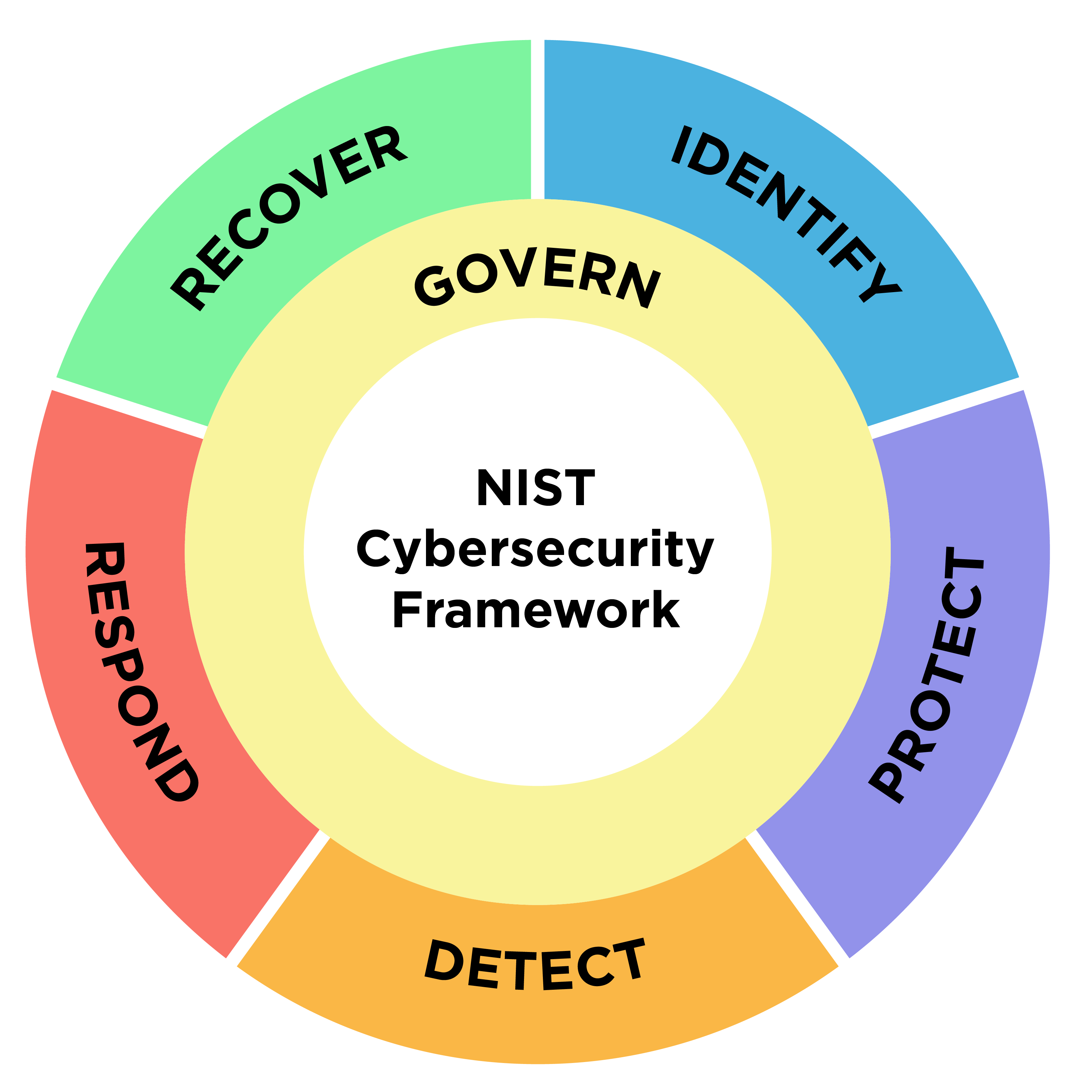 So let’s get down to it – what’s the big difference? Well, on the surface, the most obvious change is the addition of Governance to make a 6th function. From NIST’s new graphic, Governance sits as the center circle that crosses all functions. This visual representation clearly demonstrates the importance of Governance in all areas. While adding a function, the total number of categories shifted down from 108 to 106. And continuing to compare v1.1 to v2.0 by numbers alone, there are 10 categories that do not exist (in the same form) in v2.0, while there are 11 new categories in v2.0. If you’re scratching your head, let us explain. CSF 2.0 isn’t just the addition of a function and its associated categories. Think of it more like a reorganization. Some functions that may have previously been (awkwardly) placed under certain functions have been moved to Governance to put more focus on this function, while others may have been jockeyed to a different category or renamed. When looking at v2.0 and the changes as a whole, most of the concepts from v1.1 are still there – just in a different way.
So let’s get down to it – what’s the big difference? Well, on the surface, the most obvious change is the addition of Governance to make a 6th function. From NIST’s new graphic, Governance sits as the center circle that crosses all functions. This visual representation clearly demonstrates the importance of Governance in all areas. While adding a function, the total number of categories shifted down from 108 to 106. And continuing to compare v1.1 to v2.0 by numbers alone, there are 10 categories that do not exist (in the same form) in v2.0, while there are 11 new categories in v2.0. If you’re scratching your head, let us explain. CSF 2.0 isn’t just the addition of a function and its associated categories. Think of it more like a reorganization. Some functions that may have previously been (awkwardly) placed under certain functions have been moved to Governance to put more focus on this function, while others may have been jockeyed to a different category or renamed. When looking at v2.0 and the changes as a whole, most of the concepts from v1.1 are still there – just in a different way.
Understanding that many businesses use the NIST CSF to guide their cybersecurity practices, we have to consider the implications of CSF 2.0 to these businesses. For many, if they previously followed the CSF, they should be in pretty good shape. There are two primary challenges that stand out. First, v2.0 should be viewed in its entirety, not merely as the new function and its categories. With so much reorganization, the best approach is to view it as fresh and new. Understand that a security assessment should always be viewed as new to review the current state of an organization’s cybersecurity. At the same time, there are opportunities to reference back to previous year’s responses. In this case, referencing back to last year’s assessment will not be as helpful since the categories have changed. The second challenge may come when conducting any annual status updates with key stakeholders that show trends from scoring of previous years. Charts or graphs, percentages, etc, are going to look different – they may even show a dip. It will be key to be able to explain to those at the table why the numbers alone do not tell the full story. Using v2.0 will provide a new baseline for the future.
If your organization has yet to apply the NIST CSF, this is a fantastic time to do it. With the updates in place, the function and categories have received their necessary update to keep up with the pace of technology’s advancements. If your organization has already been using the NIST CSF, you are also going to benefit from the updates. But it may highlight areas that had previously received a light review and are now spotlighted. In speaking with cybersecurity practitioner Jimmy Armour, who acts as a vCISO for multiple companies, he highlighted that companies lacking in policies and procedures are going to see this exposed. Governance previously sat as one category under Identify, and it is now a whole function, with 4 categories coming directly from v1.1’s Governance category. Under v1.1’s Protection function, Information Protection Processes & Procedures was one category and it is now split into seven categories. You can see the impact. And this is just how important these areas are – deserving of much more attention and effort.
In the end, the updates might lead to more initiatives on the “To Do” list, but they are well-intended and necessary. Whether your organization has been following the NIST CSF or there has been a desire to implement for the first time, a trusted partner can help guide you through the process. And if you do not currently have a partner, Appalachia Technologies has a team of vCISOs that have been working with companies to guide them in the process and would be happy to speak with you. For any questions or help, contact us at 888-277-8320 or (Subject: NIST CSF 2.0).
For more information on the NIST CSF 2.0, as well as resources to help you on your path, visit: https://csrc.nist.gov/news/2024/the-nist-csf-20-is-here.
