Appalachia Technologies Blog
PCI DSS Compliance Without Crushing Your Budget
Achieving PCI DSS compliance can seem daunting, especially for teams with limited resources. Here are three critical PCI DSS questions and practical, low-cost solutions to help you stay secure without breaking the bank.
1. How can we minimize PCI DSS scope with limited resources?
Solution: Focus on existing tools and network controls:
- Use Built-in Firewalls: Enable and configure OS-level firewalls (e.g., Windows Firewall) to isolate PCI systems from non-PCI systems. Most modern EDR solutions include host-firewall management. This allows for the scalability and use of templates rather than managing each host individually.
- Segment Networks Using VLANs: Most managed routers and switches support network segmentation via VLANs. This technology allows you to separate the CDE from the rest of the network.
- Enforce Strong Access Controls: Use Windows Group Policy or Linux user groups to restrict access to PCI scope with limited resources & budget. Access Control Lists (ACLs), available on most current network devices, are another great resource to limit access to the CDEs.
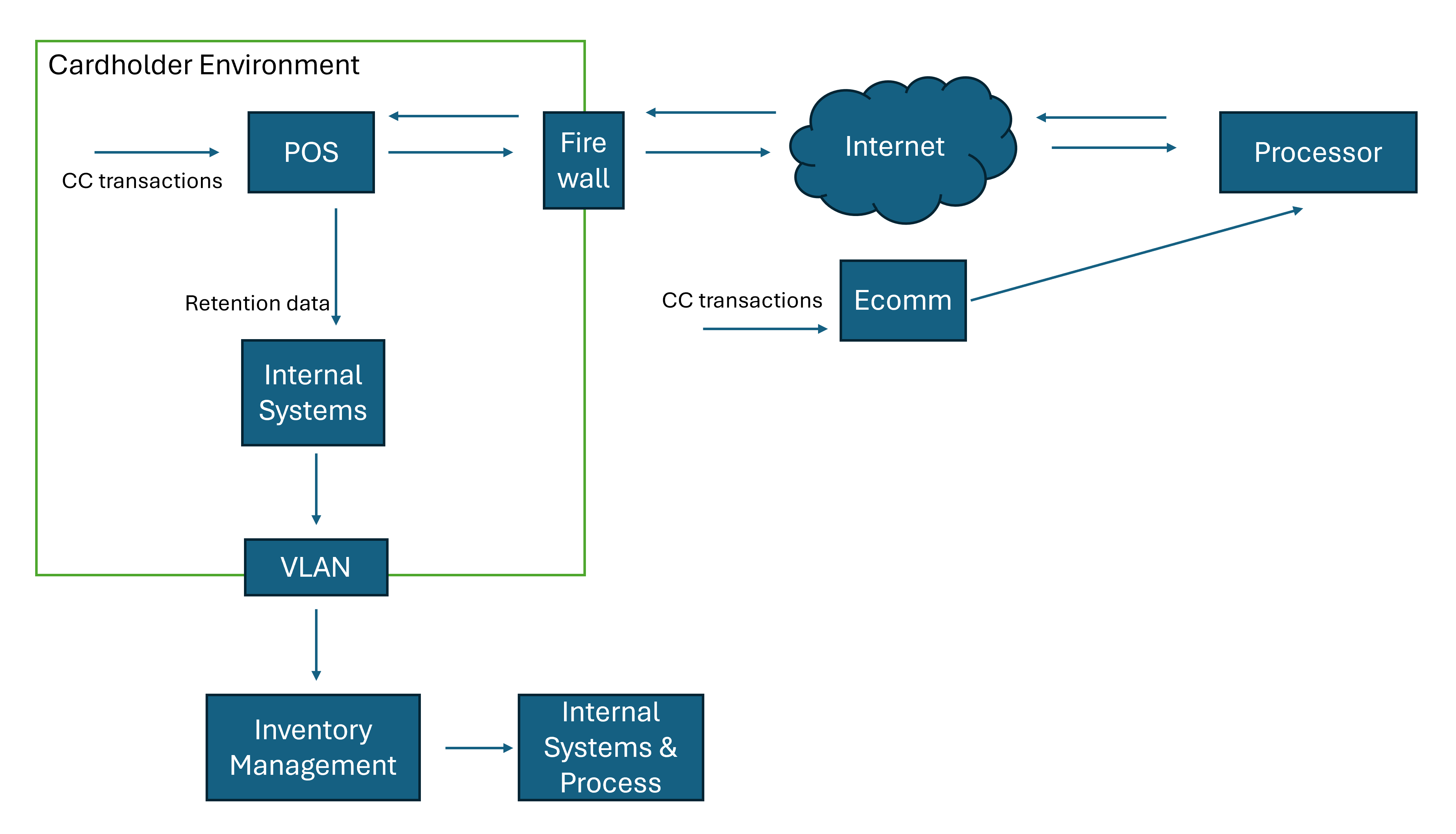
- Data Flow Review: Map cardholder data flows to identify unnecessary data storage or transmission points. Having an accurate map of where sensitive data is processed or stored is critical when identifying what assets are in scope for PCI DSS.
Bonus Tip: Document segmentation strategies to demonstrate compliance during audits. This is also applicable if you have multiple frameworks in play since a single control can be mapped across multiple standards.
2. How can we manage third-party risk without expensive tools?
Solution: Focus on contract terms, manual reviews, data ownership, responsibilities and accountability:
- Update Contracts: Ensure third-party agreements define PCI DSS responsibilities, data ownership, data protection expectations, and breach notification requirements. Make sure to read and understand all contracts, then clearly state who’s responsible and accountable. Keep in mind you are also a third-party to someone else.
- Request Evidence of Compliance: Ask vendors for their latest PCI DSS Attestation of Compliance (AOC) or Report on Compliance (ROC). Make sure this is performed as part of your Third-Party Risk Management program.
- Control Vendor Access: Limit and control vendor or third-party access using temporary credentials, enforcing MFA, using VPNs or leveraging Zero Trust environments. Other control methods include overseeing remote connections and limiting the level of access granted to “jump-boxes” or remote access gateways.
- Manual Log Reviews: Reviewing access logs manually enables you to detect suspicious behaviors from vendors. Keep in mind they are as exposed to threats as the rest of the organizations.
Bonus Tip: Conduct periodic check-ins with vendors to ensure security expectations and responsibilities remain clear. Trust but verify, vendors have also fallen victims of cyber-attacks with rare exceptions where data breaches have not impacted clients.
Need help managing your PCI compliance program? Our certified QSAs and compliance experts can guide you through scope reduction, gap assessments, and ongoing management.
Learn about our PCI DSS services →
3. How can we secure legacy systems that must stay online?
Solution: Strengthen defenses using existing resources and process improvements:
- Isolate Legacy Systems: Place legacy systems in a dedicated VLAN with limited or no direct internet access. For example, systems that have been replaced but must be kept alive for historical or audit purposes.
- Tighten Access Controls: Enforce multi-factor authentication (MFA) for administrators and restrict access using existing directory services. Create dedicated Admin accounts relevant only to the system in question.
- Manual Log Analysis: Conduct regular log reviews for unusual activity if automated monitoring tools aren’t available. Legacy systems are known for their incompatibility with current security solutions, thus the need for compensating controls.
- Plan for Decommissioning: When migrating to new solutions, legacy systems are often kept for historical access and audit purposes. Set clear deadlines and retention policies for the system to be removed completely.
Bonus Tip: Create a phased plan to eventually replace or decommission legacy systems.
Final Thoughts
PCI DSS compliance doesn’t have to drain your budget. By strengthening policies, improving processes, and maximizing the tools you already have, you can effectively manage PCI DSS requirements without significant spending. Focus on smart strategies, clear documentation, and staff awareness to keep your environment secure and compliant.
When you understand the benefits of PCI compliance – customer trust, reputational security, risk mitigation, and facilitating partnerships as a few – the value makes the investment an easy ‘yes.’ But implementing these strategies while managing day-to-day operations can be overwhelming.
Ready to simplify your PCI compliance journey? Whether you need a full assessment, gap remediation, or ongoing program management, our team of certified QSAs is here to help. Explore our PCI DSS services and request a consultation →
Have questions? Contact us at or 888-277-8320.
Related Reading: 5 Steps to Build a PCI Program That Makes Managing Compliance Easy
 Over the course of his career, Yoel Alvarez has worked in various areas in Cybersecurity and Compliance for large, medium, and small companies, leveraging frameworks including NIST, ISO, HIPPA, SOX, SOC, GDPR, and PCI DSS.
Over the course of his career, Yoel Alvarez has worked in various areas in Cybersecurity and Compliance for large, medium, and small companies, leveraging frameworks including NIST, ISO, HIPPA, SOX, SOC, GDPR, and PCI DSS.
Yoel's expertise lies in his ability to effectively translate complex cybersecurity concepts into practical strategies that are aligned with the goals of the business. He is recognized for his exceptional ability to build collaborative relationships with stakeholders, foster a security-conscious culture within organizations, and provide cybersecurity awareness to stakeholders at all levels. Yoel's professionalism, extensive experience, and commitment to excellence make him a trusted advisor in the cybersecurity space.

