Appalachia Technologies Blog
Review of Verizon's 2021 Data Breach Investigations Report (DBIR)
One of the great “must reads” for us cybersecurity wonks is the annual DBIR (Data Breach and Incident Response), issued by Verizon every year since 2008. While never dull, the DBIR is not a light read and comes in at a meaty 115 pages this year. While we at Appalachia are delighted to stuff our horns with popcorn and study every last page, we realize that not everyone can make the time to fully digest this comprehensive treatise. To that end, we have taken the time to write an executive summary of the DBIR for readers of our blog – because we care, and we don’t want you missing reruns or tee time.
This year’s DBIR is broken up into 8 major sections: Introduction, Results and Analysis, Incident Classification Patterns, Industries, SMB, Regions, Wrap-up, and Appendices. Let’s dig in by getting a sense of the sheer amount of work that the DBIR team puts in here:
“This year we analyzed 79,635 incidents, of which 29,207 met our quality standards and 5,258 were confirmed data breaches, sampled from 88 countries around the world. Once again, we include breakouts for 11 of the main industries, the SMB section, and we revisit the various geographic regions studied in the prior report to see how they fared over the last year. We also include our Center for Internet Security (CIS) Controls® recommendation mapping, because the world being unpredictable and uncertain doesn’t mean your security strategy has to be.”
The DBIR team is dealing with an absolute mountain of data here and distilling that data down into actionable intelligence for executive decision making was not easy. The Incident Classifications Patterns section alone is over 30 pages long, where the team classifies these nearly eighty thousand incidents into eight distinct patterns:
Social Engineering: “Psychological compromise of a person, which alters their behavior into taking an action or breaching confidentiality.”
Basic Web Application Attacks: “Simple web application attacks with a small number of steps/additional actions after the initial web application compromise.”
System Intrusion: “System Intrusion captures the complex attacks that leverage Malware and/or Hacking to achieve their objectives including deploying ransomware.”
Miscellaneous Errors: “Incidents where unintentional actions directly compromised a security attribute of an information asset. This does not include lost devices, which is grouped with theft instead.”
Privilege Misuse: “Incidents predominantly driven by unapproved or malicious use of legitimate privileges.”
Lost and Stolen Assets: “Any incident where an information asset went missing, whether through misplacement or malice.”
Denial of Service: “Attacks intended to compromise the availability of networks and systems. Includes both network and application layer attacks.”
Everything Else: “…. covers all incidents that don’t fit within the orderly confines of the other patterns.”
It should also be noted that these patterns are hardly static for a year over year basis, as can be discerned from DBIR Figure 44:
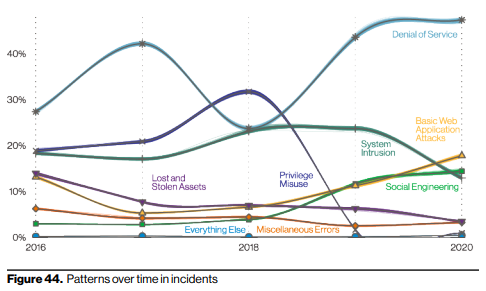
From a simple empirical prospective, this is pretty consistent with what we at Appalachia have been seeing ourselves out in the wild -- so we expect that our readers are facing the same challenges. Our cybersecurity team has become adept at dealing with every one of these things on behalf of our clients. One thing that stands out in the way that the DBIR team has classified these incidents, is that technology alone cannot solve these problems -- organizations MUST train their people, and they MUST build a culture of security. Thankfully, there are a variety of existing well-known frameworks including the NIST CSF (Cybersecurity Framework) and the CMMC (Cybersecurity Maturity Model Certification), technical and administrative roadmaps which are well positioned to help build that much needed culture of security.
The next major part of the paper, “Industries”, breaks down the ways in which various industries are being victimized through the 8 incident pattern types identified earlier. These industries are: Accommodation, Administrative, Agricultural, Construction, Education, Entertainment, Finance, Healthcare, Information, Management, Manufacturing, Mining, other Services, Professional, Public, Real Estate, Retail, Wholesale Trade, Transportation, Utilities, and lastly “Unknown”.
Table 4 sums up those findings nicely:
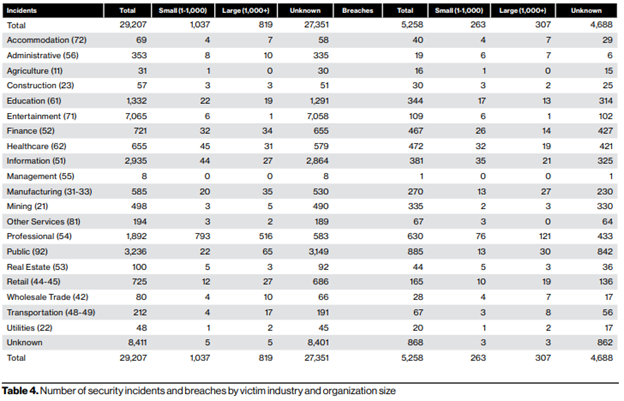
One thing the team is careful to point out, is that readers should not infer anything about the security posture of a given industry as a result of the DBIR data, due to the sampling size and methods.
Next up is “SMB” or Small to Midsize Businesses, which is a brief 2 pages. Essentially the DBIR team says that SMB’s are just as much in the crosshairs as large businesses, and that the perpetrators tend to be financially motivated (not a surprise) regardless of the target type. In the cybersecurity world, we worry about SMB’s a lot.
In section 6, we delve into Regions, broken down as: Asia Pacific (APAC), Europe, Middle East and Africa (EMEA), and North America (NA). Here is what the DBIR concludes about each region:
APAC Region -- The most common type of breaches that took place in APAC were caused by Financially motivated attackers Phishing employees for creds, and then using those stolen creds to gain access to mail accounts and web application servers.
EMEA Region -- EMEA continues to be beset by Basic Web Application Attacks, System Intrusion and Social Engineering.
NA Region -- Northern American organizations continue to be the target of Financially motivated actors searching for money or easily monetizable data. Social Engineering, Hacking and Malware continue to be the favored tools utilized by these actors.
The team points out that not all regions of the world are represented in the report, but this is simply because no data has been contributed on their behalf.
Section 7 (Year in Review) is the last part before the appendices. The DBIR Year in Review reads like a “Who’s Who” gala of pretty much everything that made news in the cyberworld for 2020. When we see how many independent events are listed here for each month, and then realize the entire list is twelve times that, it’s pretty astonishing:
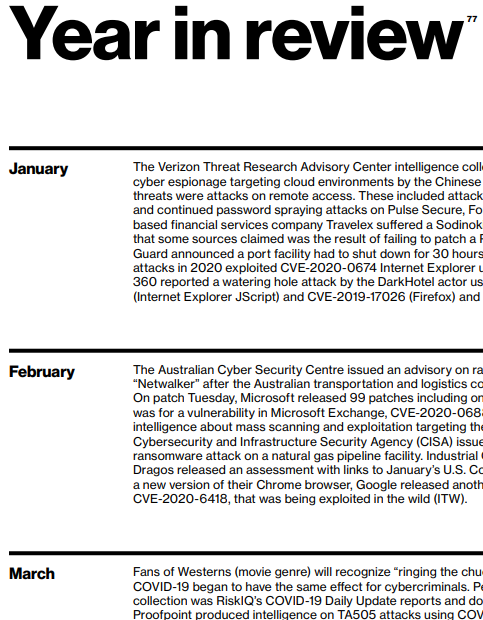
That is pretty much the meat and potatoes of the report, but let’s talk about a few of the independent “highlights” from the Verizon 2021 DBIR.
Page 25 has some interesting findings about BEC (Business Email Compromise):
“When losses did occur, they were not of the one-size-fits-all variety. Following the rules of good business, we expect attackers to charge what the market can bear. For a small organization that is usually a small amount. For a large organization, however, losses can be much more substantial. When examining breaches that included a reported loss, 95% of BECs fell between $250 and $985,000 dollars with $30,000 being the median. That is a pretty big range, you say? Maybe so, but Computer Data Breach (CBD) ranges were even wider with 95% falling between $148 and $1.6 million, and a median loss of $30,000. Finally, for ransomware the median amount lost was $11,150, and the range of losses in 95% of the cases fell between $70 and $1.2 million.”
Patterns over time in breaches:
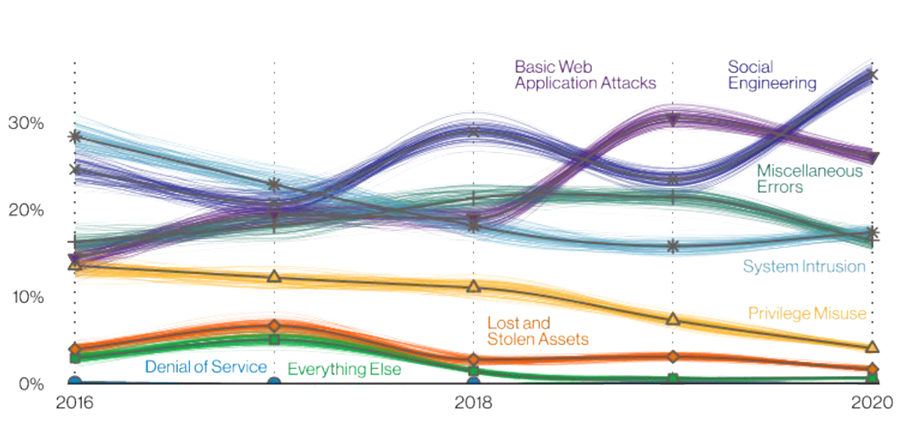
This graph on page 20 shows us in percentages, what are the origin years of the unpatched vulnerabilities that were RECENTLY exploited. Eternal Blue is 37,217,565 of these, so 2017 would be in 2nd place without that. The big takeaway here, is that attackers are still having a LOT of success using OLD exploits that should have been patched long ago. When we at Appalachia do assessments, we often find I.T. environments with deficient patch and vulnerability management. The importance of proper patch and vulnerability management cannot be overstated.
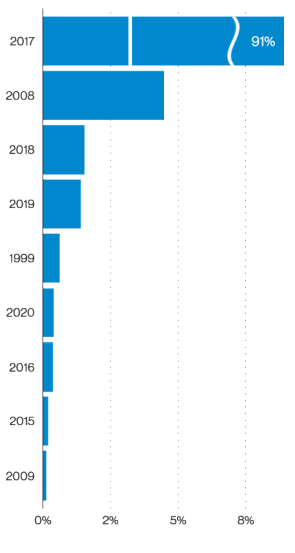
Page 49 :
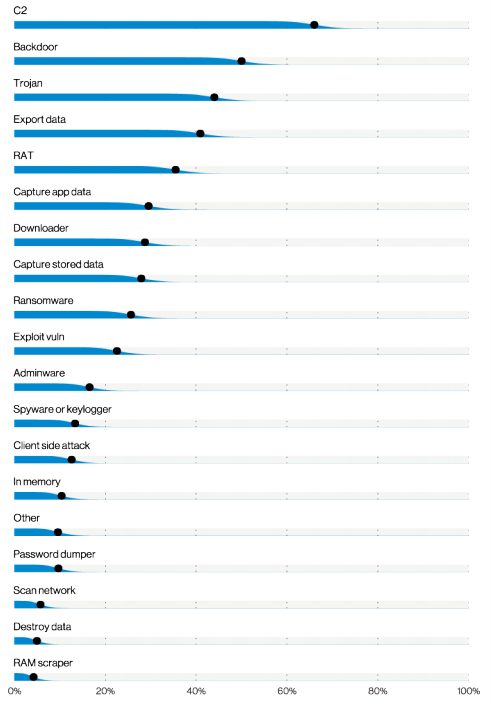
“Phishing is responsible for the vast majority of breaches in this pattern, with cloud-based email servers being a target of choice. Business Email Compromises (BECs) were the second most common form of Social Engineering. This attack scenario reflects the meteoric rise of Misrepresentation, which was 15 times higher than last year in Social incidents. Additionally, Social Engineering attacks often result in the loss of Credentials. This pattern saw those stolen credentials used in both Hacking and Malware attacks.”
This graph on page 49 shows malware varieties used in social engineering incidents. Now, we expect the C2 (Command and Control), Trojan, and Backdoor stuff. BUT, take a look near the bottom, where we see non-zero amounts of some of the really creepy stuff like “Client Side Attack”, “RAM Scraping”, etc. – Mr. or Mrs. Badguy has to have physical access to your equipment to do these things. Not good at all.
So, there is your 30,000 foot view of the 2021 Verizon Data Breach Investigations Report. Now go hit the green and act like you read the whole thing. Look again here next year for another Executive Summary of the DBIR.
Jason McNew
Senior Engineer, Cybersecurity Risk and Compliance, Appalachia Technologies
 Jason McNew is a CISSP and a CMMC RP (Registered Practitioner). Jason, a United States Air Force veteran, holds a Master’s degree from Penn State University in Information Sciences, Cyber Security and Information Assurance, in addition to a Bachelor of Science and two Associate of Science degrees. Penn State’s Cyber Security program has been reviewed and endorsed by the National Security Agency (NSA) and the Department of Homeland Security (DHS). He also worked for the White House Communications Agency from 2003 until 2015. In 2017 he founded Stronghold Cyber Security, which was acquired by Appalachia Technologies in 2020.
Jason McNew is a CISSP and a CMMC RP (Registered Practitioner). Jason, a United States Air Force veteran, holds a Master’s degree from Penn State University in Information Sciences, Cyber Security and Information Assurance, in addition to a Bachelor of Science and two Associate of Science degrees. Penn State’s Cyber Security program has been reviewed and endorsed by the National Security Agency (NSA) and the Department of Homeland Security (DHS). He also worked for the White House Communications Agency from 2003 until 2015. In 2017 he founded Stronghold Cyber Security, which was acquired by Appalachia Technologies in 2020.
